The
Cyber Caliphate
(U.S.
CENCOM Hacked)
In
April of this year, I mentioned a new division of ISIS called 'the
Cyber Caliphate'.
It
has been in existence since 2015 and is likely to be playing a
bigger role in identifying civilian and non-civilian targets for
assassination and murder in the future.
Since
last year I have been working on an article to identify the extent to
which this Cyber Caliphate has been active.
I
was shocked to discover that it had hacked the U.S. Central Command
in 2015.
(This,
by the way, is the equivalent of al-Qaeda hacking civilian air
control prior to another 9/11.)
I
realized the extent of the problem and was nearing the completion of
an article about the extensive nature of this hack.
Through
a number of unforeseen circumstances the data I had 'fell into
unauthorized hands'. For a researcher or analyst 'unauthorized'
means any person not a researcher – not permitted to hold
'privileged' material necessary for the conduct of our research work.
It's
even more a problem when the data you were sent anonymously is the
property of the government of another country.
Property
Of The Government Of........................
Most
Police forces in Europe (including the United Kingdom) are not
equipped to handle material of this nature.
Many
such Officers are Freemasons, members of political parties, some
have links with far left and far right groups some even links with
the criminal fraternity and others with foreign intelligence agencies
and operatives – maybe through a boyfriend or girlfriend or close
friends they meet up with in their social life.
Data
such as that I am including here should always be immediately
extracted and be returned to the Government of the country from where
it originated.
There
is another reason for this:
An
attack could be imminent on one or more of the persons on such lists
by terrorist groups.
How
Many US Central Command Lists have Been Hacked By ISIS?
I
don't know – but probably quite a few.
I
have personal details of some 20,000 U.S. Senior Military and
Intelligence Personnel sent to me anonymously with the message that
this is part of what the Islamic Cyber Caliphate has hacked from
U.S. CENCOM.)
Likely
Scenario: (remind you of 9/11?)
The
very fact that, lets say for example, the Police in a Western allied
country, should they come into possession of such data, might either
be slow or indeed not have even divulged this fact to their own
intelligence services (that they are in possession of current active
lists of U.S. military personnel) for reasons of administrative
kudos, could easily result in inadvertently placing the lives of such
military Officers in significant and immediate danger – simply
because they did not know what they were handling nor it's
significance and were too limited in the scope of their own
responsibilities.
This
is the classic 9/11 scenario.
All
the information was there – but compartmentalised - because of
bureaucracy (human error.)
What
Exactly Did The Cyber Caliphate (ISIS) HACK from CENCOM?
So
here it is folks, part of what the Islamic Cyber Caliphate has
hacked from U.S. Central Command database.
I
have left enough information in so that you can identify one of the
lists from which the data was extracted. There are many other lists.
(I
am assuming by now that all these personal email addresses have been
changed.)
So
What Could ISIS Do With Such Hacking Abilities?
Apart
from the obvious targeting for assassination through honey traps and
(possibly) blackmail, there are many other scenarios (far-fetched as
some may seem) too numerous to mention.
The
prospect of being able to 'crash' nuclear power stations, hospitals,
military and civilian radar systems and, yes, the big one,
autonomously launching or prematurely detonating nuclear missiles in their silos,
may not be as far away as you and I think.
The
point I am making in releasing this data at this particular time is
that the hacking (and indeed leaking) of petabytes of data poses real
and significant threats to national and international security in the
immediate now and into the future and there appears to be very little
to guarantee 100% security of any data stored digitally.
If
a foreign power, in collusion (either knowingly or unwittingly) with
others, can, with impunity, 'take down' a U.S. Presidential Candidate
(Hillary Clinton) do not lightly dismiss the capabilities nor reach
of a (false-flag) terrorist network and their supporters – however
far-fetched the premise might seem – to take down entire
infrastructures. [It is believed that at least one Western coalition nation has sub-contracted a Middle East country to work out how to do likewise to Iran's conventional military ballistic launch infrastructure.]
©Patrick
Emek, September 2017
(I have edited the data below so as not to endanger individuals whose details (and more - data files - not included here) have been in the hands of (the now defunct) the Islamic State's 'Cyber Caliphate' since 2015.)
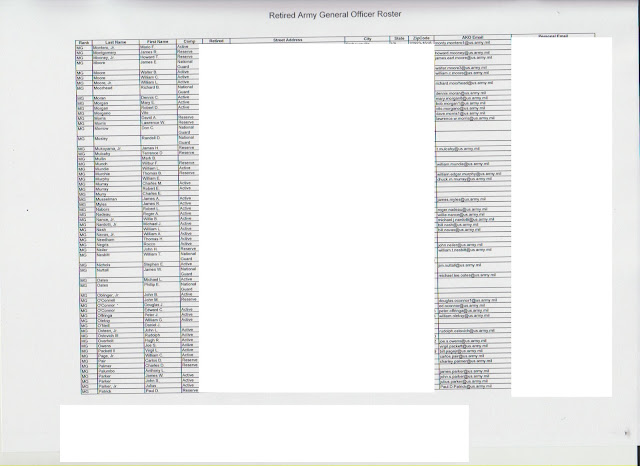
The 'Go' Army Roster was also hacked by ISIS Cyber Caliphate hackers in late 2014-early 2015.
you can see the Roster list at:
https://drive.google.com/file/d/0B1PQwrS3VCwcR3E0cTNfb25FSDQ/view?usp=sharing
Because all the information is official and there are no personal details on this file (home addresses, next of kin etc etc) I am including it in full .
There are however other databases of U.S. military support organizations believed to have been hacked since their security is not as good as U.S. CENCOM.
Such databases are not shown at this website but are in the public domain.
security details I have omitted:
full home addresses and personal emails
The 'Go' Army Roster was also hacked by ISIS Cyber Caliphate hackers in late 2014-early 2015.
you can see the Roster list at:
https://drive.google.com/file/d/0B1PQwrS3VCwcR3E0cTNfb25FSDQ/view?usp=sharing
Because all the information is official and there are no personal details on this file (home addresses, next of kin etc etc) I am including it in full .
There are however other databases of U.S. military support organizations believed to have been hacked since their security is not as good as U.S. CENCOM.
Such databases are not shown at this website but are in the public domain.
security details I have omitted:
full home addresses and personal emails